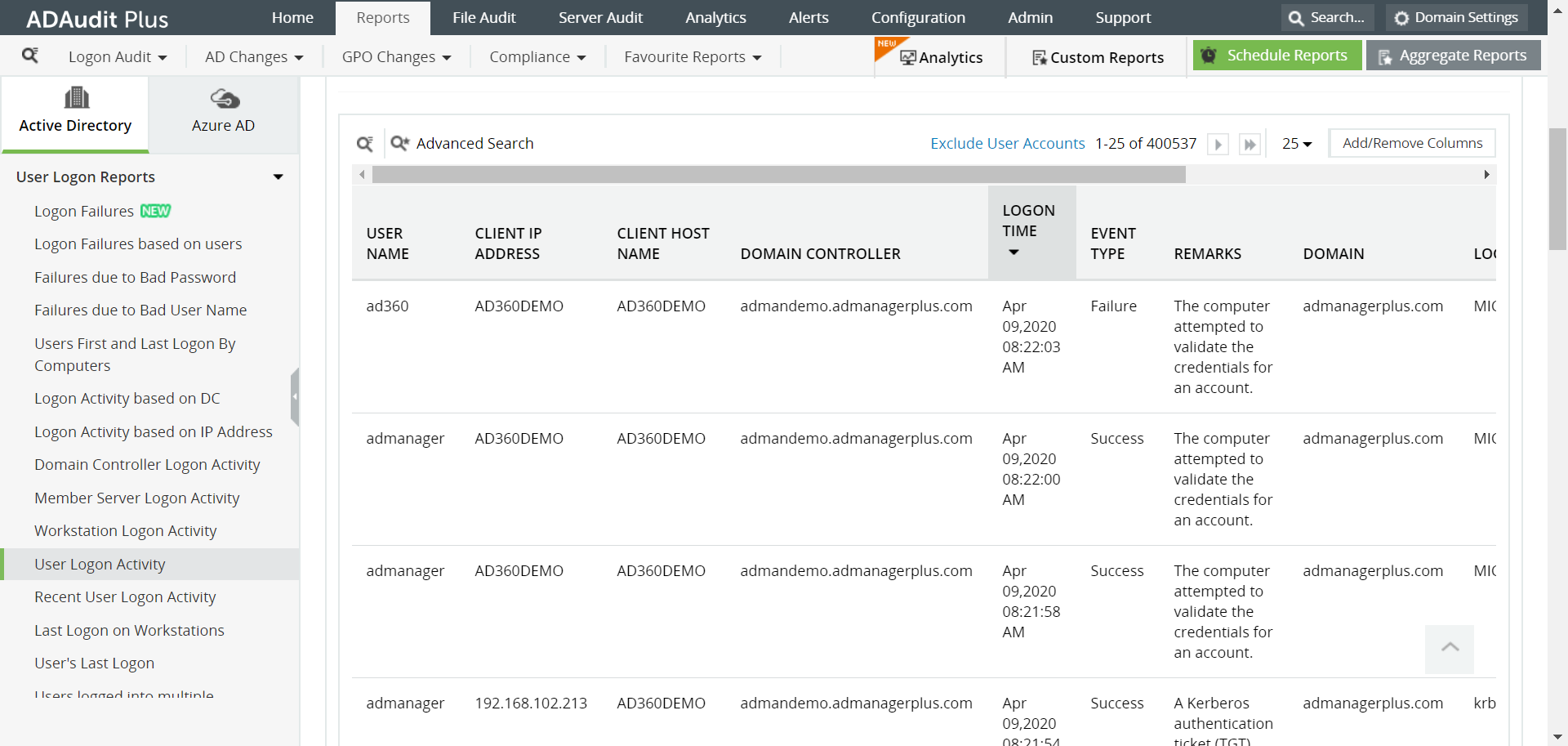
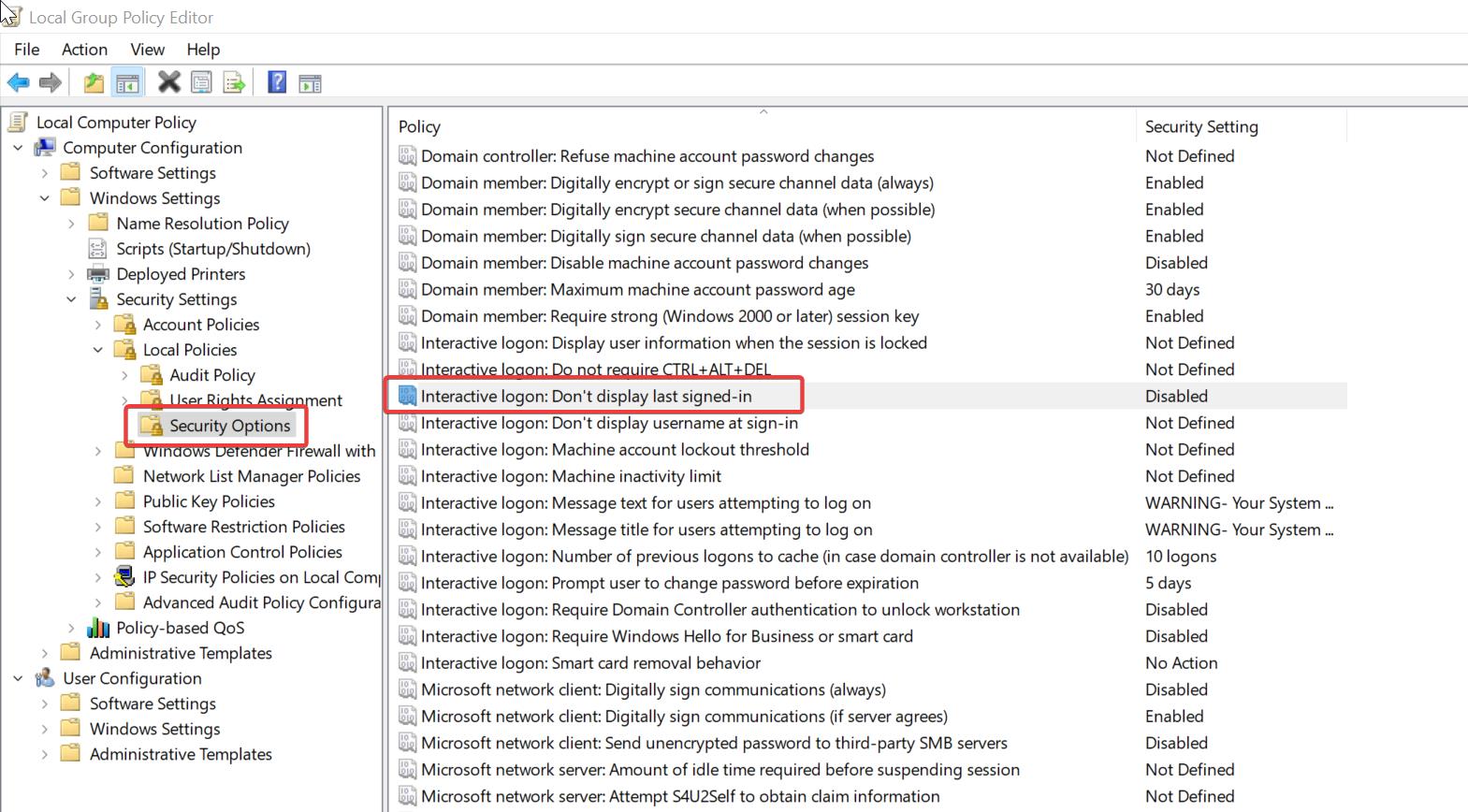
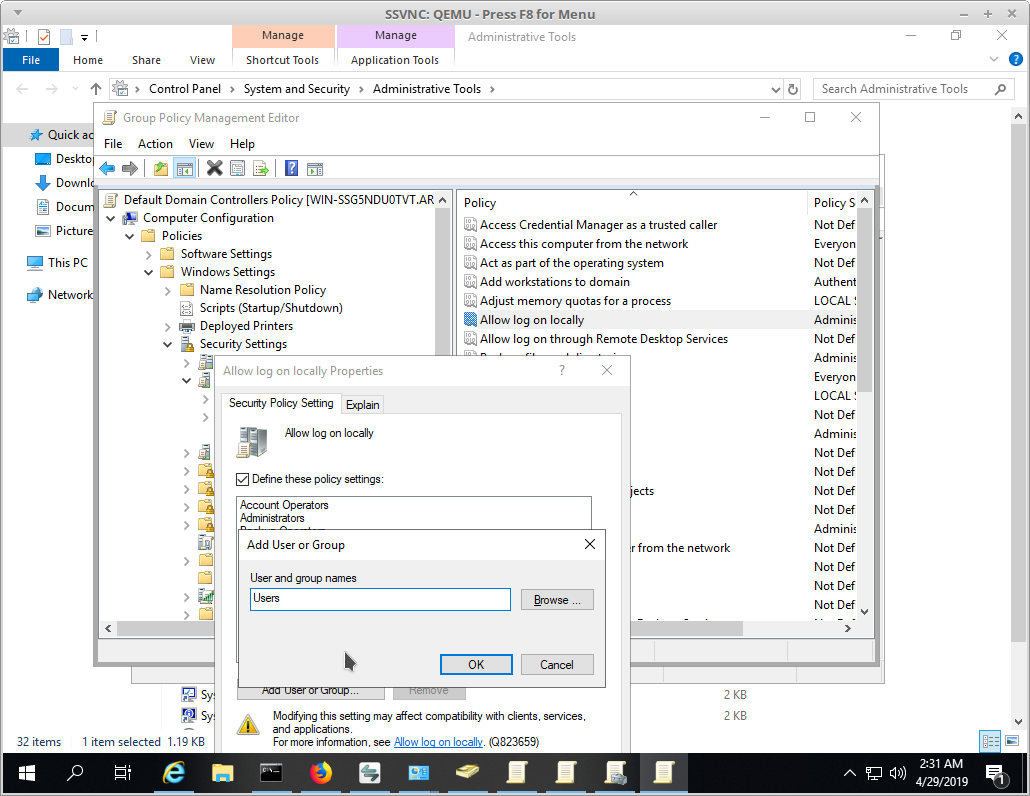
Deny Interactive Login
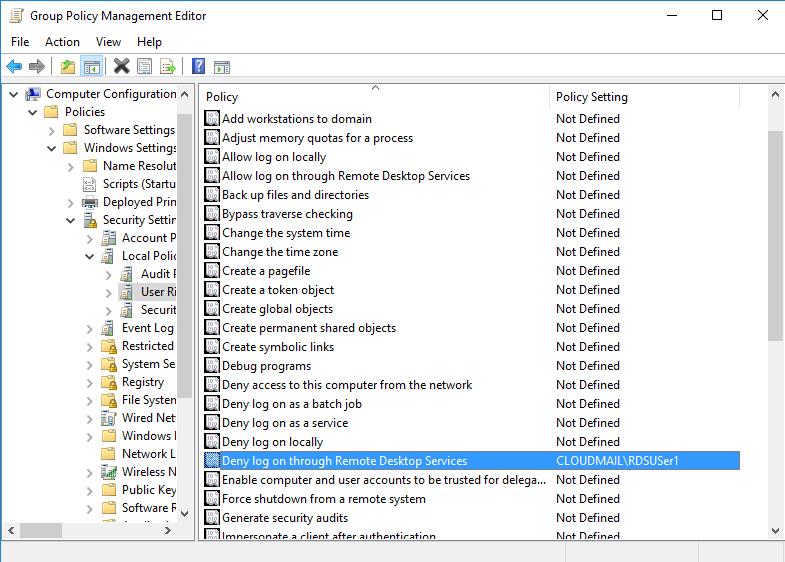
Deny Interactive Login - There are several options under “gpo > computer configuration > policies > windows settings > security. It has precedence over the “log on through terminal. Here you will find an “allow” and “deny” right for each logon type making for a total of 10 logon rights. One has been listed where you break out the settings into another gpo then deny access to those machines in the new gpo. The easiest way to deny service accounts interactive logon privileges is with a gpo. Deny interactive logon to the workstations locally and through rdp. However, we would like to deny interactive logon for this account. There are five logon types in windows. Modify gpos or create a new gpo for the target servers to have the ‘denylogon’ group added to the deny interactive logon. Another way would be to make a separate ou and. This is the opposite of allow log on locally and any user with both rights will be denied the right to logon. Authentications to the windows desktop (whether via console or remote desktop access) are known as interactive logons. If a user ends up with both the allow and deny. Modify gpos or create a new gpo for the target servers to have the ‘denylogon’ group added to the deny interactive logon. In the gpo, go to computer configuration > policies > windows settings > security settings > local policies > user rights assignment. add. This article describes the recommended practices, location, values, policy management, and security considerations for the deny log on as a service security policy. “run as” is a local login so you cannot deny that and still use it. One has been listed where you break out the settings into another gpo then deny access to those machines in the new gpo. Create a new ad group call ‘denylogon’ or similar. Another way would be to make a separate ou and. Script requires local admin access to the remote servers so it can perform tasks that requires admin rights. “deny logon through terminal services” denies a user the ability to log on using terminal services or remote desktop. Deny interactive logon to the workstations locally and through rdp. In the policy, i'm denying interactive logon to an ad group called deny. Deny interactive logon to the workstations locally and through rdp. This is the opposite of allow log on locally and any user with both rights will be denied the right to logon. It has precedence over the “log on through terminal. In the gpo, go to computer configuration > policies > windows settings > security settings > local policies >. The easiest way to deny service accounts interactive logon privileges is with a gpo. Script requires local admin access to the remote servers so it can perform tasks that requires admin rights. I created a group policy in the same ou as the user account and group. I created a group called “disable interactive logon” and added my test user. One has been listed where you break out the settings into another gpo then deny access to those machines in the new gpo. Configure your service accounts to deny interactive logons. Group policy allows us to restrict who can log on interactively,. In the policy, i'm denying interactive logon to an ad group called deny interactive logon (i know creative).. Script requires local admin access to the remote servers so it can perform tasks that requires admin rights. If a user ends up with both the allow and deny. “run as” is a local login so you cannot deny that and still use it. When a service account is configured to allow interactive logins like logon types 2, 10, and. Another way would be to make a separate ou and. However, we would like to deny interactive logon for this account. Modify gpos or create a new gpo for the target servers to have the ‘denylogon’ group added to the deny interactive logon. Create a new ad group call ‘denylogon’ or similar. I created a group policy in the same. This policy is not linked to the domain controllers ou. This article describes the recommended practices, location, values, policy management, and security considerations for the deny log on as a service security policy. I created a group policy in the same ou as the user account and group. Configure your service accounts to deny interactive logons. Modify gpos or create. Here you will find an “allow” and “deny” right for each logon type making for a total of 10 logon rights. One has been listed where you break out the settings into another gpo then deny access to those machines in the new gpo. If a user ends up with both the allow and deny. “deny logon through terminal services”. Configure your service accounts to deny interactive logons. Group policy allows us to restrict who can log on interactively,. Deny interactive logon to the workstations locally and through rdp. I created a group called “disable interactive logon” and added my test user account to this group. “run as” is a local login so you cannot deny that and still use. It has precedence over the “log on through terminal. Deny interactive logon to the workstations locally and through rdp. Group policy allows us to restrict who can log on interactively,. “run as” is a local login so you cannot deny that and still use it. Another way would be to make a separate ou and. If a user ends up with both the allow and deny. I created a group policy in the same ou as the user account and group. However, we would like to deny interactive logon for this account. Describes the best practices, location, values, policy management, and security considerations for the deny log on locally security policy setting. “deny logon through terminal services” denies a user the ability to log on using terminal services or remote desktop. Configure your service accounts to deny interactive logons. In the gpo, go to computer configuration > policies > windows settings > security settings > local policies > user rights assignment. add. Another way would be to make a separate ou and. When a service account is configured to allow interactive logins like logon types 2, 10, and 11, this presents a. This article describes the recommended practices, location, values, policy management, and security considerations for the deny log on as a service security policy. Group policy allows us to restrict who can log on interactively,. It has precedence over the “log on through terminal. Modify gpos or create a new gpo for the target servers to have the ‘denylogon’ group added to the deny interactive logon. The easiest way to deny service accounts interactive logon privileges is with a gpo. Create a new ad group call ‘denylogon’ or similar. Deny interactive logon to the workstations locally and through rdp.Remote Desktop Logins RDP Access by Privileged Users
Deny logon with a smartphone YubiOn FIDO Logon Guide
Deny User Logon To Specific Computers On A Domain How to Login with a Local Account instead of
How to Show all users on Login Screen in Windows 11? Technoresult
Deny and allow workstation logons with Group Policy 4sysops
Deny User Logon To Specific Computers On A Domain How to Login with a Local Account instead of
Deny Interactive Logon for Service Accounts GenSys Cyber Security Security Advisories
Paula's IT Blog Deny Interactive Logon for Service Accounts
Paula's IT Blog Deny Interactive Logon for Service Accounts
RDS 2012 R2 Preventing Interactive Login Griffon's IT Library
One Has Been Listed Where You Break Out The Settings Into Another Gpo Then Deny Access To Those Machines In The New Gpo.
This Policy Is Not Linked To The Domain Controllers Ou.
There Are Several Options Under “Gpo > Computer Configuration > Policies > Windows Settings > Security.
Authentications To The Windows Desktop (Whether Via Console Or Remote Desktop Access) Are Known As Interactive Logons.
Related Post: