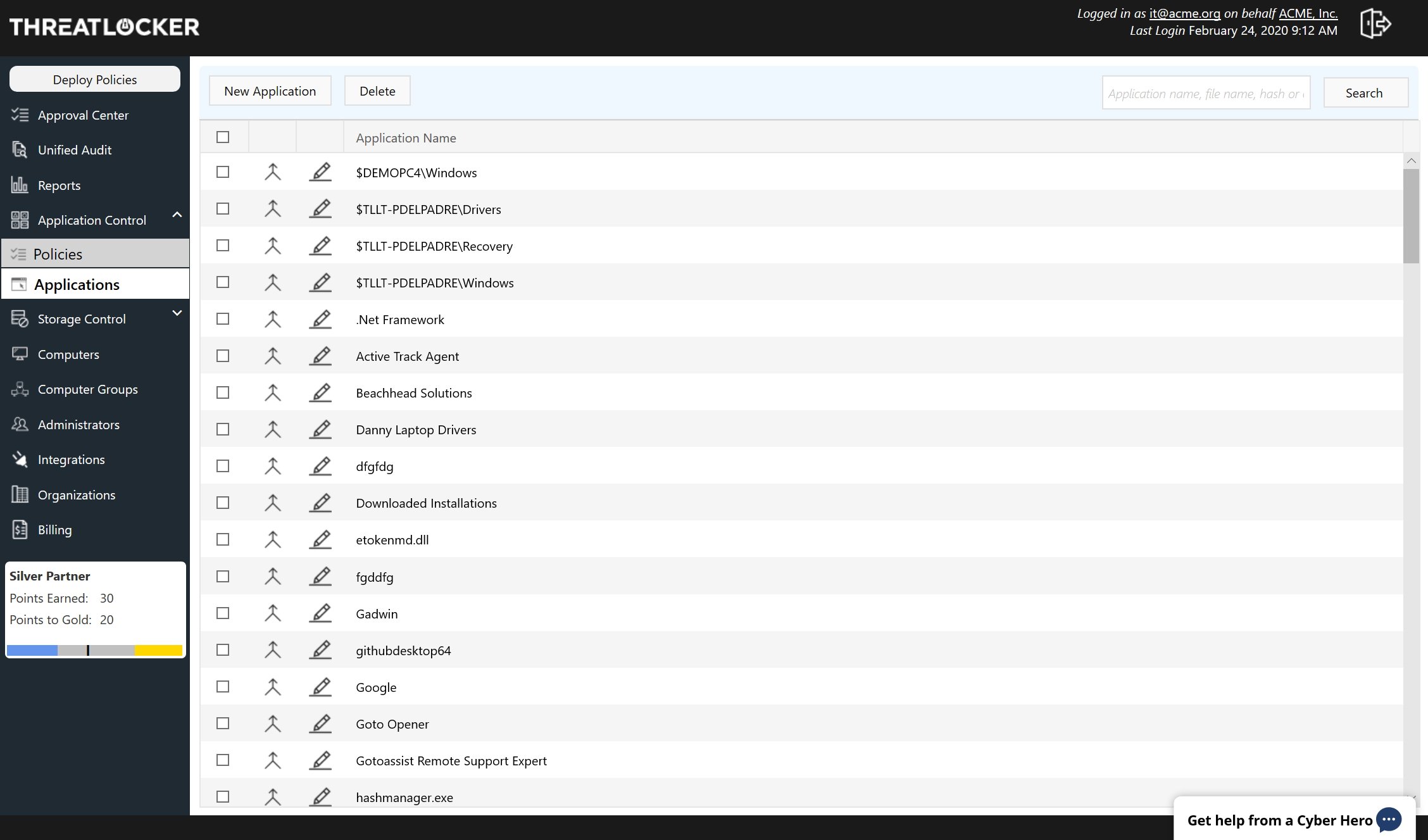
Threatlocker Login
Threatlocker Login - When you first deploy with threatlocker, you place the endpoints in learning mode for a couple months, which is designed to learn all the programs that normally run on these devices, and automatically create policies to permit them in the future, once you lock things down. Byod inherently has users with admin rights (even if they don't actively login as the admin), it being a personal device means they can install whatever they want and threatlocker would just throw alarms and stop them. We have about 2k endpoints we manage over a few hundred clients. Threatlocker is aware of the problem and troubleshooting it, but this has now been since 7 am this morning. It almost defeats the purpose of both Initially, i had weekly calls with them to review the portal and refine policies. I reached out to threat locker support to see about how to remove their product when tamper protection is enabled. I am considering rolling threatlocker at my msp. We are a small msp who took over a client from another msp that was using threat locker. 99% of customers are extremely comfortable with this arrangement, as it means support can help them when they have a problem, and sales engineers can help get them set up and secured. Threatlocker is aware of the problem and troubleshooting it, but this has now been since 7 am this morning. For any size team i highly recommend incorporating cyberhero support into your processes. I am currently testing tl and i am extremely impressed with everything it does. They said it cannot be done. Initially, i had weekly calls with them to review the portal and refine policies. So i am curious for those who have actually rolled it out, is it worth the extra $$ and what are your thoughts on it? We are a small msp who took over a client from another msp that was using threat locker. Policies.txt file not updating across clients. When you first deploy with threatlocker, you place the endpoints in learning mode for a couple months, which is designed to learn all the programs that normally run on these devices, and automatically create policies to permit them in the future, once you lock things down. It almost defeats the purpose of both We are a small msp who took over a client from another msp that was using threat locker. The old msp refuses to remove the product from the machines because of a dispute with the client and the msp. We have about 2k endpoints we manage over a few hundred clients. Seems like a terrible product for byod environments. Initially,. Seems like a terrible product for byod environments. Threatlocker is aware of the problem and troubleshooting it, but this has now been since 7 am this morning. With that being said, it is $$ and pretty complicated ( at least out of the box ). Byod inherently has users with admin rights (even if they don't actively login as the. We are a small msp who took over a client from another msp that was using threat locker. We have about 2k endpoints we manage over a few hundred clients. Threatlocker is aware of the problem and troubleshooting it, but this has now been since 7 am this morning. Seems like a terrible product for byod environments. For any size. So i am curious for those who have actually rolled it out, is it worth the extra $$ and what are your thoughts on it? Byod inherently has users with admin rights (even if they don't actively login as the admin), it being a personal device means they can install whatever they want and threatlocker would just throw alarms and. Wanted to see what others are doing to work around the issue. At the very least you should be running threatlocker to protect your own msp. Policies.txt file not updating across clients. 99% of customers are extremely comfortable with this arrangement, as it means support can help them when they have a problem, and sales engineers can help get them. I reached out to threat locker support to see about how to remove their product when tamper protection is enabled. We are a small msp who took over a client from another msp that was using threat locker. Threatlocker is needed, and there is a way to manage the total cost of ownership properly. For any size team i highly. So i am curious for those who have actually rolled it out, is it worth the extra $$ and what are your thoughts on it? When you first deploy with threatlocker, you place the endpoints in learning mode for a couple months, which is designed to learn all the programs that normally run on these devices, and automatically create policies. So i am curious for those who have actually rolled it out, is it worth the extra $$ and what are your thoughts on it? We have about 2k endpoints we manage over a few hundred clients. 99% of customers are extremely comfortable with this arrangement, as it means support can help them when they have a problem, and sales. Policies.txt file not updating across clients. We are a small msp who took over a client from another msp that was using threat locker. The old msp refuses to remove the product from the machines because of a dispute with the client and the msp. 99% of customers are extremely comfortable with this arrangement, as it means support can help. When you first deploy with threatlocker, you place the endpoints in learning mode for a couple months, which is designed to learn all the programs that normally run on these devices, and automatically create policies to permit them in the future, once you lock things down. Wanted to see what others are doing to work around the issue. Threatlocker is. I am currently testing tl and i am extremely impressed with everything it does. I am considering rolling threatlocker at my msp. Wanted to see what others are doing to work around the issue. Threatlocker is aware of the problem and troubleshooting it, but this has now been since 7 am this morning. It almost defeats the purpose of both The old msp refuses to remove the product from the machines because of a dispute with the client and the msp. I reached out to threat locker support to see about how to remove their product when tamper protection is enabled. For any size team i highly recommend incorporating cyberhero support into your processes. So i am curious for those who have actually rolled it out, is it worth the extra $$ and what are your thoughts on it? Policies.txt file not updating across clients. Seems like a terrible product for byod environments. Byod inherently has users with admin rights (even if they don't actively login as the admin), it being a personal device means they can install whatever they want and threatlocker would just throw alarms and stop them. Threatlocker is needed, and there is a way to manage the total cost of ownership properly. We are a small msp who took over a client from another msp that was using threat locker. When you first deploy with threatlocker, you place the endpoints in learning mode for a couple months, which is designed to learn all the programs that normally run on these devices, and automatically create policies to permit them in the future, once you lock things down. 99% of customers are extremely comfortable with this arrangement, as it means support can help them when they have a problem, and sales engineers can help get them set up and secured.Download ThreatLocker APK Free for Android
Securing Your Digital Environment With Threatlocker Concensus Technologies
Enterpriselevel cybersecurity solutions ThreatLocker Protect
Login To ThreatLocker Account ThreatLocker Account
ThreatLocker Integricity Technology
Endpoint Protection Platform with Zero Trust ThreatLocker
Login Threatlocker Account Threatlocker Login Account How Do I Login to My ThreatLocker Account?
ThreatLocker Ops
Threatlocker Live Demo YouTube
ThreatLocker Pricing, Reviews, Features & Alternatives B2Saas
They Said It Cannot Be Done.
Initially, I Had Weekly Calls With Them To Review The Portal And Refine Policies.
At The Very Least You Should Be Running Threatlocker To Protect Your Own Msp.
With That Being Said, It Is $$ And Pretty Complicated ( At Least Out Of The Box ).
Related Post:



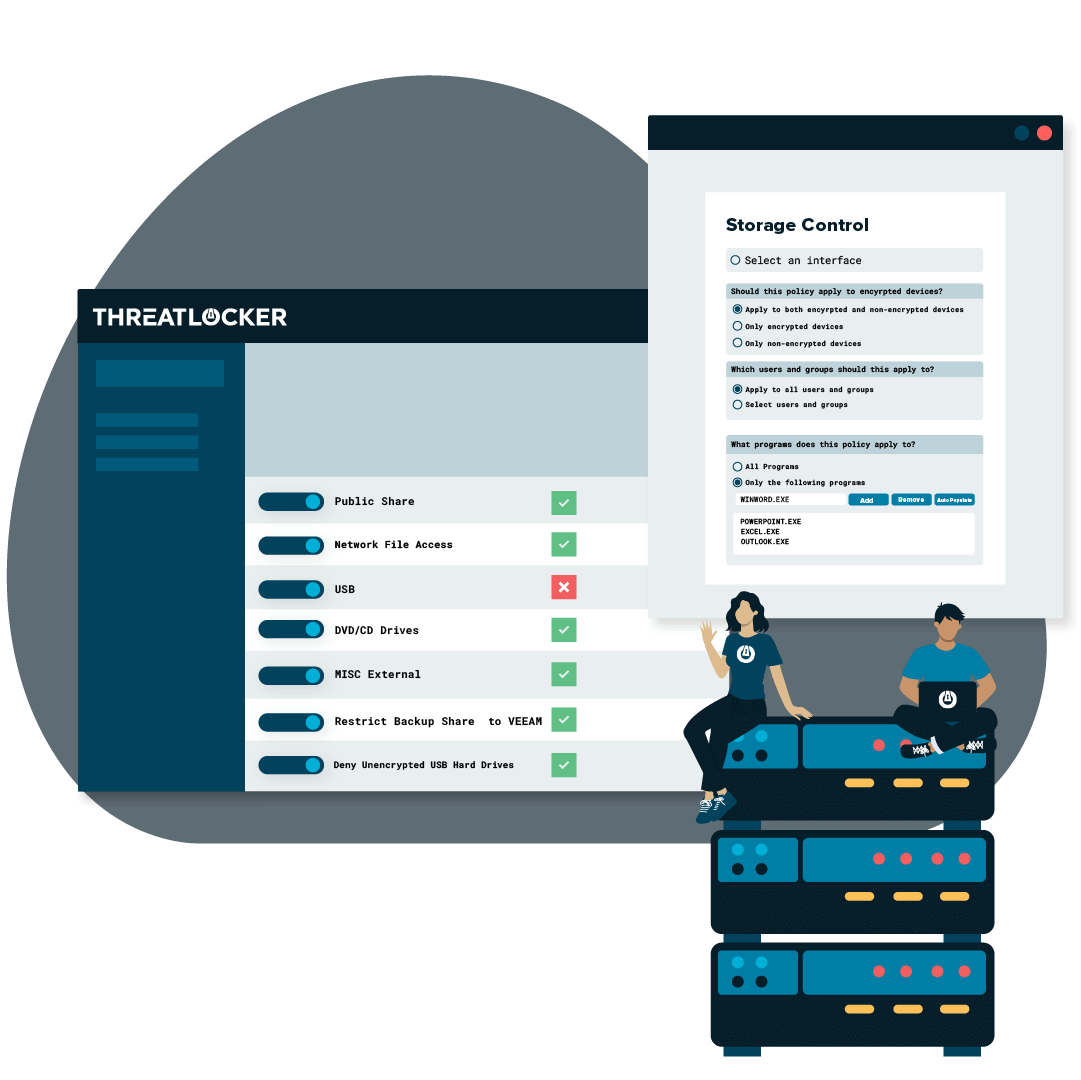
.png)